Limiting Requests per Unit Time
In the actions dropdown list of page rules, we can find the Limit Request Count option under the “CC Attack Defense Actions” category. This feature is used to control the number of requests within a specified time period, serving as an effective traffic control mechanism.
Configuration Details
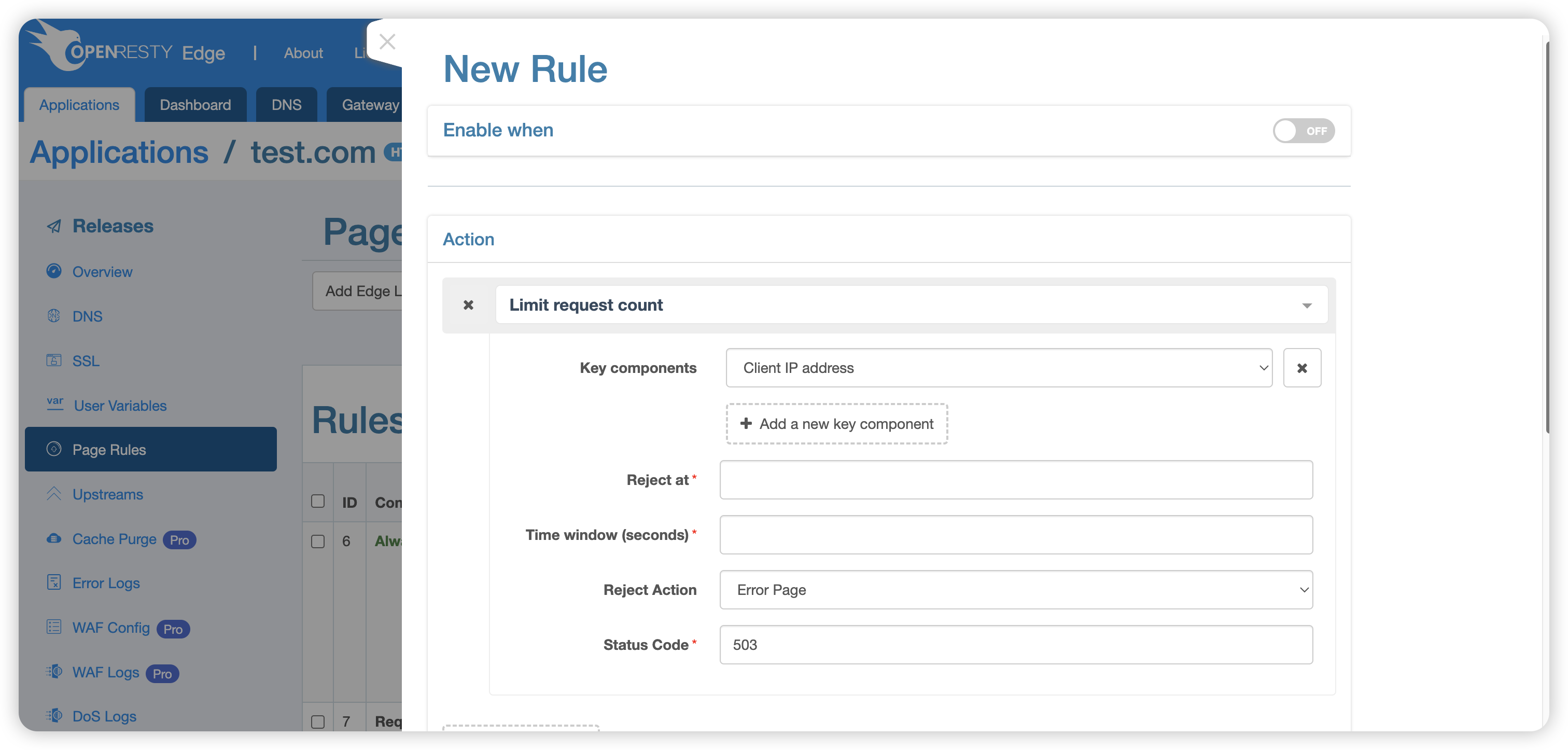
Key conponents: By default, the client’s IP address is used, but other options can be selected from the dropdown menu, such as URI, URI parameters, etc. Multiple keywords can be selected. When selecting URI parameters or Cookies, an additional Argument field needs to be specified. For detailed explanations, please refer to the Key Conponents.
Rejection Threshold: When the number of requests within the specified time window exceeds this value, the system will return a 503 error to the client.
Time Window: The time interval for counting, in seconds. The counter resets to zero at the beginning of each new time window.
Reject Action: Specifies the action to be taken when the
Rejection Thresholdis reached. For details, please check the Reject Actions.
Key Conponents
The system will limit the rate based on the set keywords. Available keywords include:
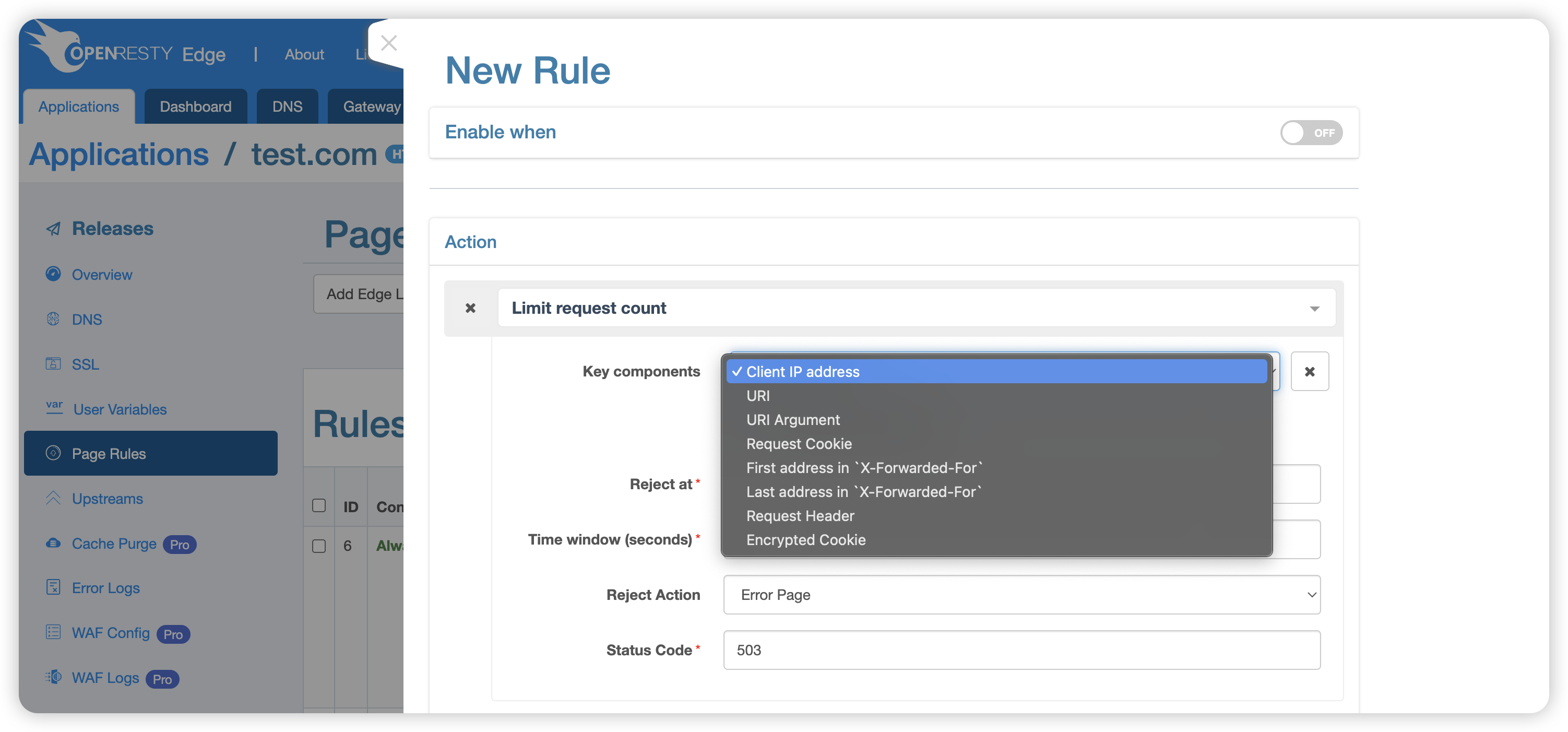
- Client IP address, e.g.,
1.1.1.1 - Request URI, e.g.,
/openresty - URI query parameters, e.g.,
arg1in/openresty?arg1=val1 - Request Cookie, e.g., key
c1incookie: c1=v1 - The first IP address in the
X-Forwarded-Forrequest header, e.g.,1.1.1.1inX-Forwarded-For: 1.1.1.1, 1.1.1.2 - The last IP address in the
X-Forwarded-Forrequest header, e.g.,1.1.1.2inX-Forwarded-For: 1.1.1.1, 1.1.1.2 - Specific HTTP request headers, e.g.,
Host - Encrypted Cookie: Rate limiting based on encrypted cookies generated by OpenResty Edge. Note that encrypted cookies must be used in combination with other keywords because the system needs to fall back to other rate limiting strategies when client requests do not carry encrypted cookies.
Reject Actions
When the rate limit condition is met, the system can perform the following preset actions (default is Return Error Page):
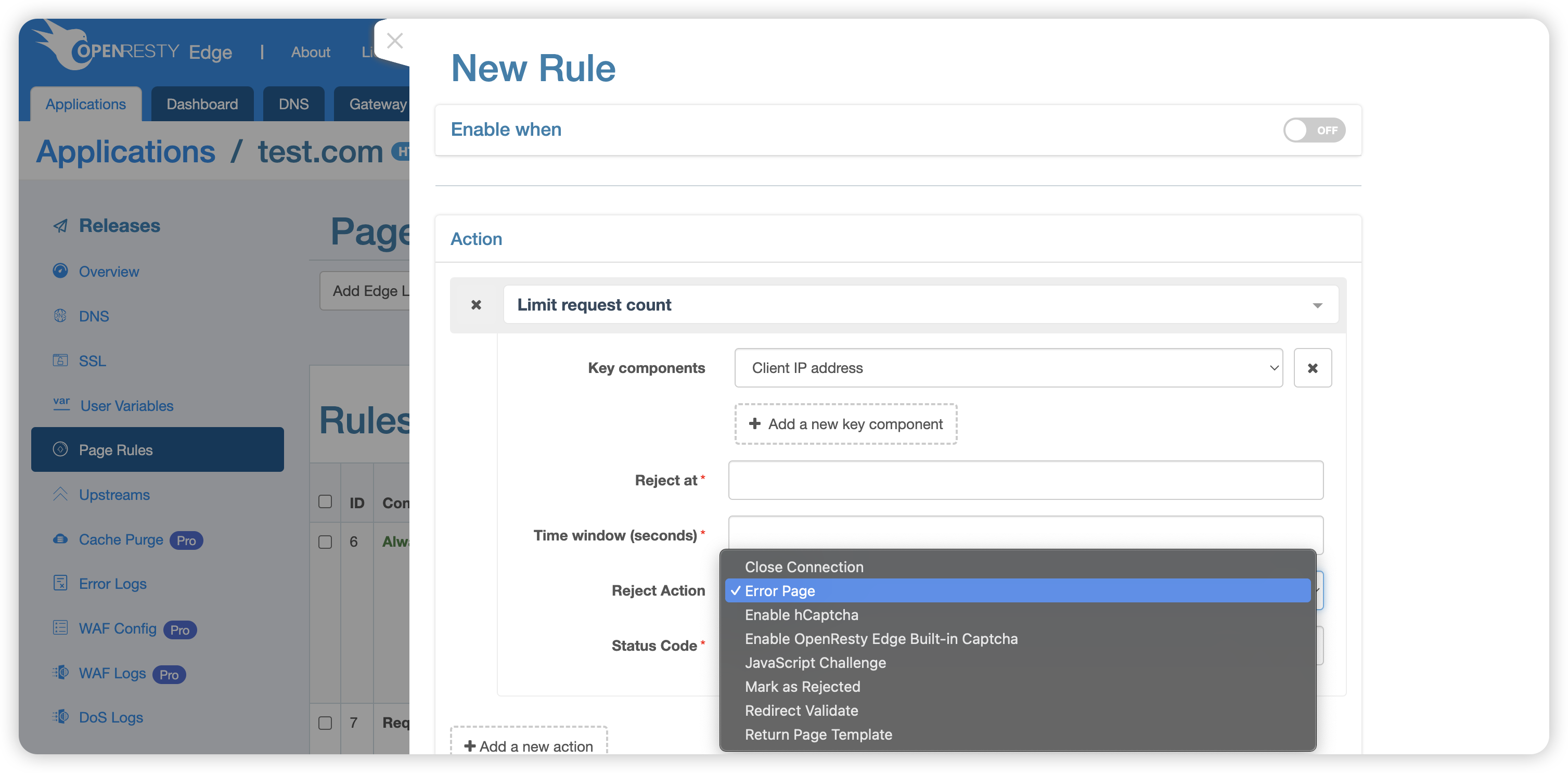
- Close Request Connection: Immediately terminate the connection with the client, no longer responding to requests.
- Return Error Page (default status code 503): Display an error page with a 503 status code to the user, indicating that the server is temporarily unable to process the request.
- Complete hCaptcha Verification: Require users to pass an hCaptcha challenge to distinguish between human and machine behavior.
- Complete OpenResty Edge Captcha Verification: Use OpenResty Edge’s captcha system to verify user identity.
- Redirect Verification: Redirect the request to a verification page, allowing access only after verification is passed.
- JavaScript Challenge: Require the user’s browser to execute JavaScript code to verify non-robot operations.
- Mark as Rejected: Only mark the request as rejected but continue to execute subsequent page rules. This action was introduced in version 24.9.1-7.
Configuration Example
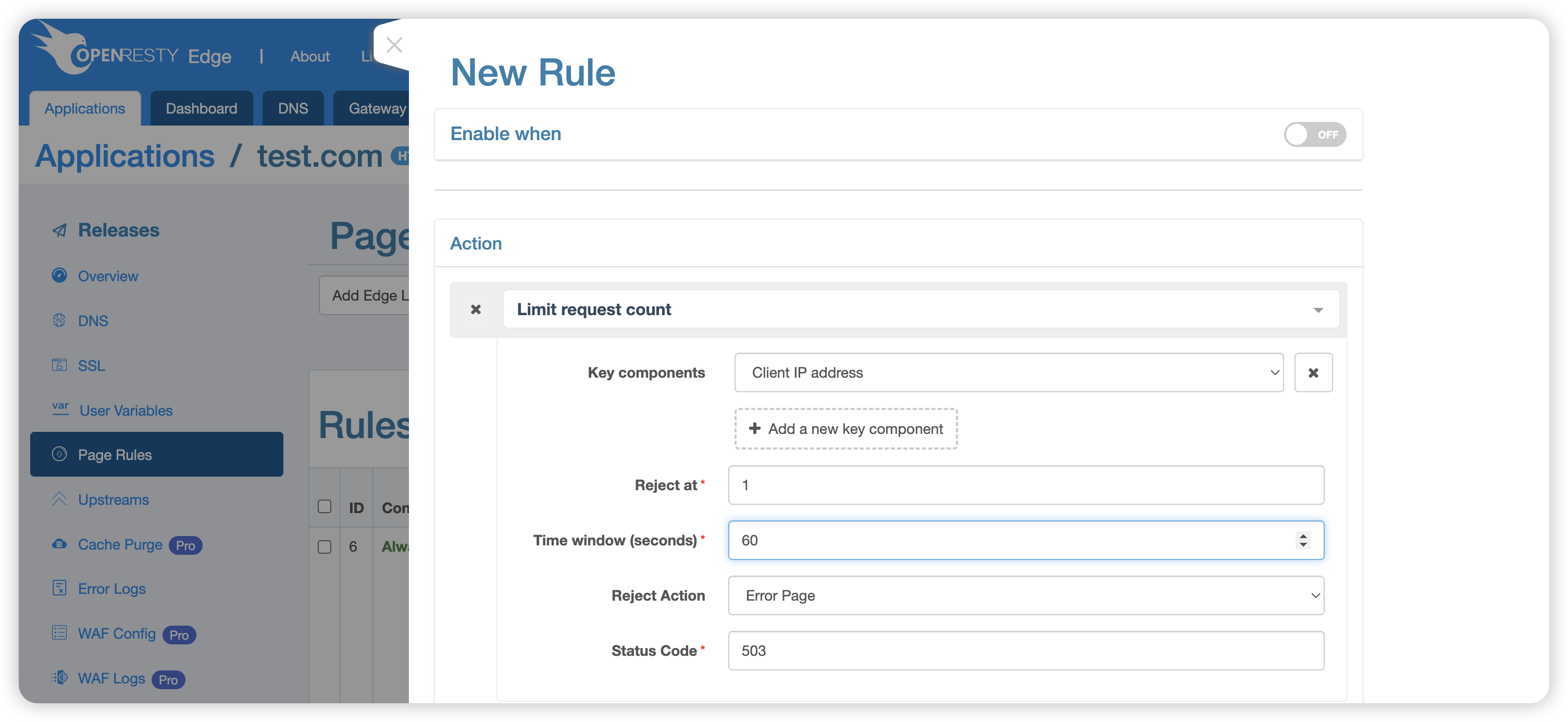
The above configuration means: Within each 60-second time window, if requests from the same terminal exceed 1, the system will return a 503 error.
After publishing the configuration, we can test the effect by simulating client access using curl commands.
The first access will not trigger the limit but will return a 404 error because the requested page does not exist:
$ curl -i -H 'host: test.com' http://node-host/404.html
HTTP/1.1 404 Not Found
Date: Fri, 04 Sep 2020 04:43:20 GMT
Content-Type: text/html
Content-Length: 150
Connection: keep-alive
Server: openresty+
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>openresty</center>
</body>
</html>
Immediately sending the same request again will trigger the rate limit, returning a 503 error:
$ curl -i -H 'host: test.com' http://node-host/404.html
HTTP/1.1 503 Service Temporarily Unavailable
Date: Fri, 04 Sep 2020 04:43:21 GMT
Content-Type: text/html
Content-Length: 194
Connection: keep-alive
Server: openresty+
<html>
<head><title>503 Service Temporarily Unavailable</title></head>
<body>
<center><h1>503 Service Temporarily Unavailable</h1></center>
<hr><center>openresty</center>
</body>
</html>
Through this example, we can clearly see the actual effect of the rate limiting function.