Enable OpenIDC Authentication
OpenResty Edge supports the OpenID Connect protocol and can act as an OpenID dependency to obtain user information from the OpenID provider to authenticate the user.
It is part of the application’s Page Rules, so let’s create a new page rule directly to see how it works.
There are many options in the Actions drop-down list, let’s pull down to Other and select Enable OpenIDC Authentication from it.
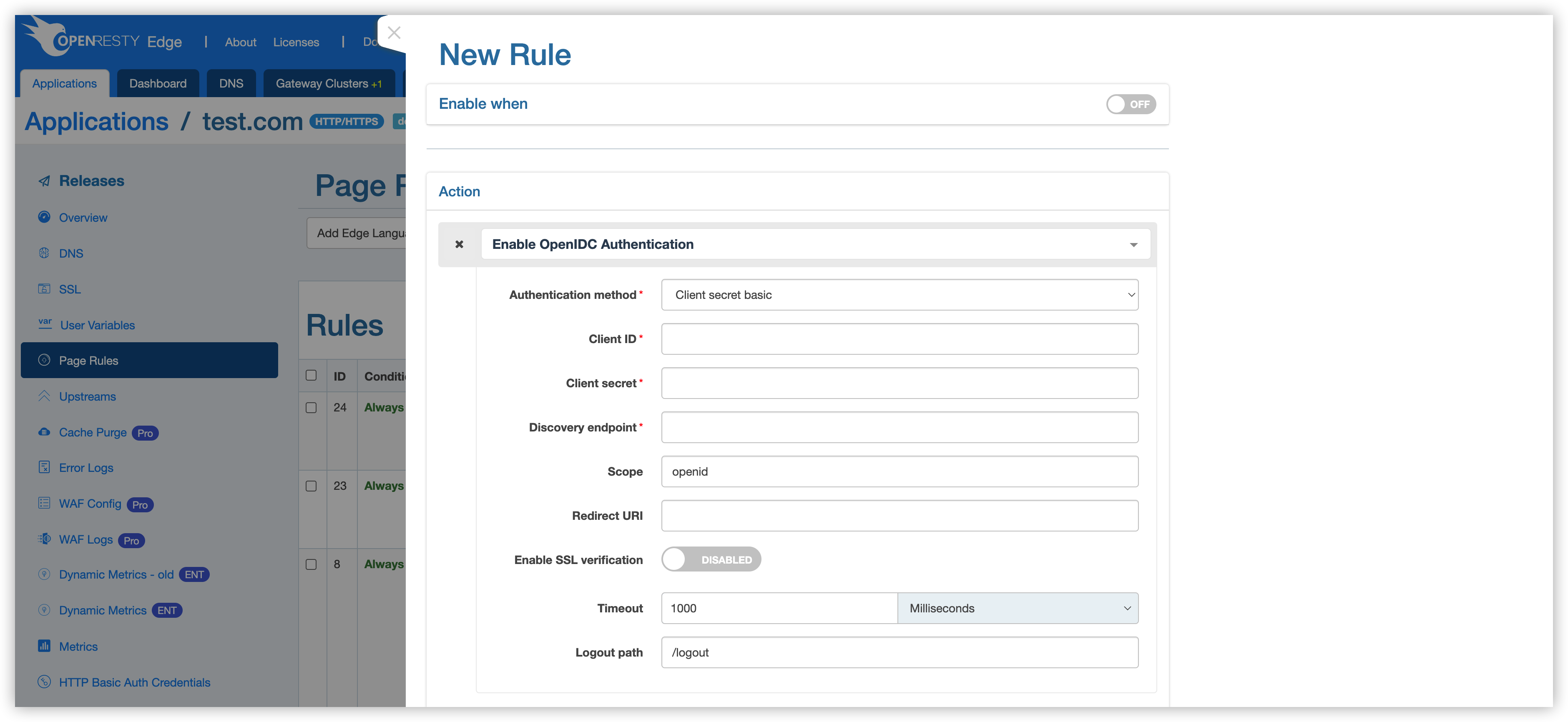
The parameters for enable-openidc-authentication are rather numerous, and the meaning of each parameter is as follows.
- Authentication Method:
client_secret_basic,client_secret_post,client_secret_jwtare currently supported. - Client ID: the client identity, obtained from the OpenID service provider.
- Client secret: client key, obtained from the OpenID service provider.
- Discovery endpoint: the URL provided by the OpenID service provider to obtain the OpenID protocol specifications supported by the service provider.
- Scope: client permissions, which must contain the OpenID.
- Redirect URI: the jump address after successful authentication supports relative and absolute addresses, can be left blank, default original request URL.
- Enabled SSL verification: whether OpenResty Edge™ uses an encrypted connection with the OpenID service provider.
- Timeoute: the timeout of the connection between OpenResty Edge™ and the OpenID service provider.
- Logout path: request domain name + logout path to log out from the OpenID service provider and to log back in when authenticating again.
In the following example, using Keycloak as the OpenID service provider, with Openidc authentication enabled, all corresponding requests need to authenticate to Keycloak first.