WAF rule set
This tool is used to quickly write and compile WAF rules.
1. Code
name: test
req-method() eq "GET" =>
waf-mark-risk(msg: "test new waf rule")
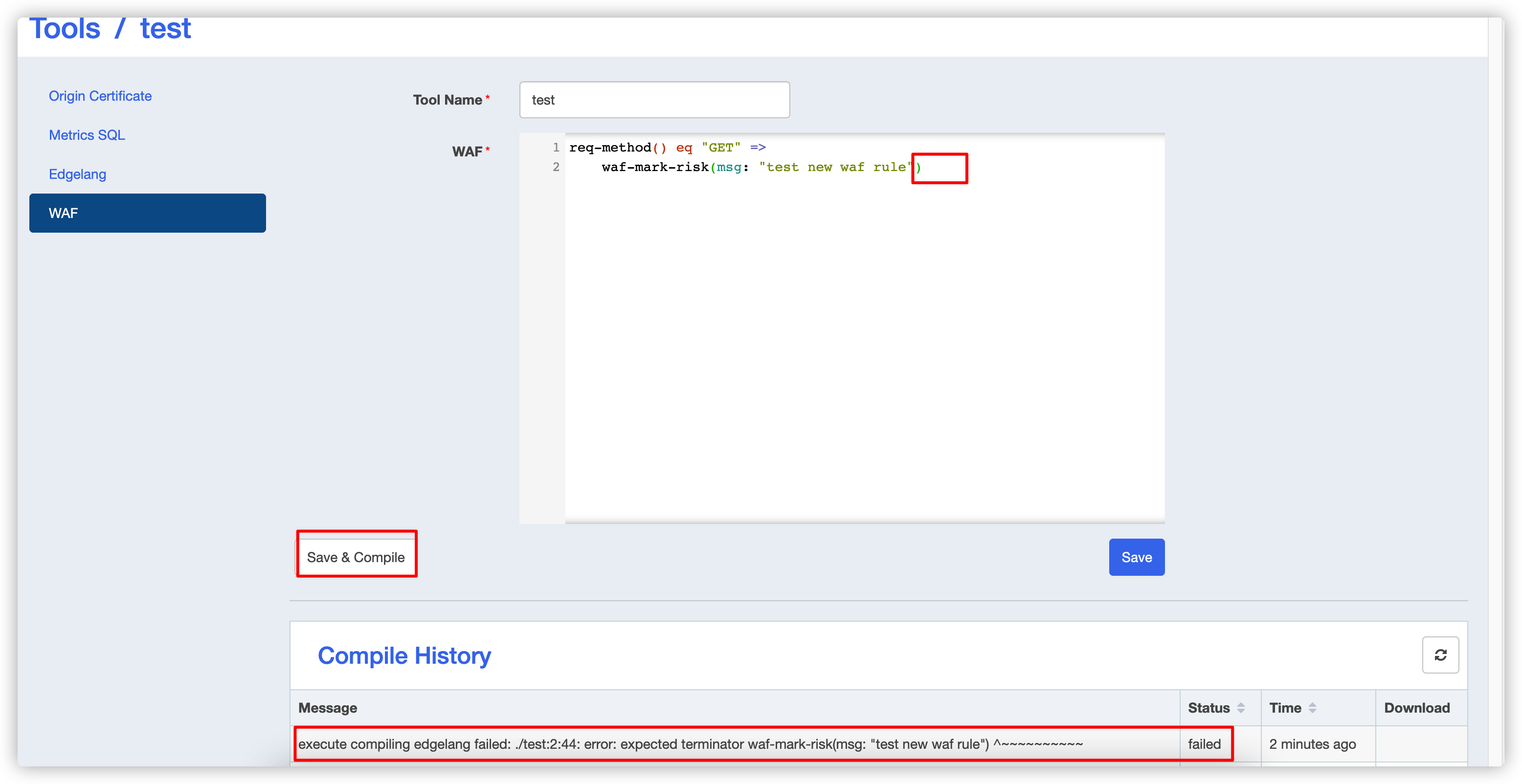
Note that there should be a ; at the end of this code, but there isn’t now, so expect an error to be reported when compiling.
2. Compile
- Compile failure
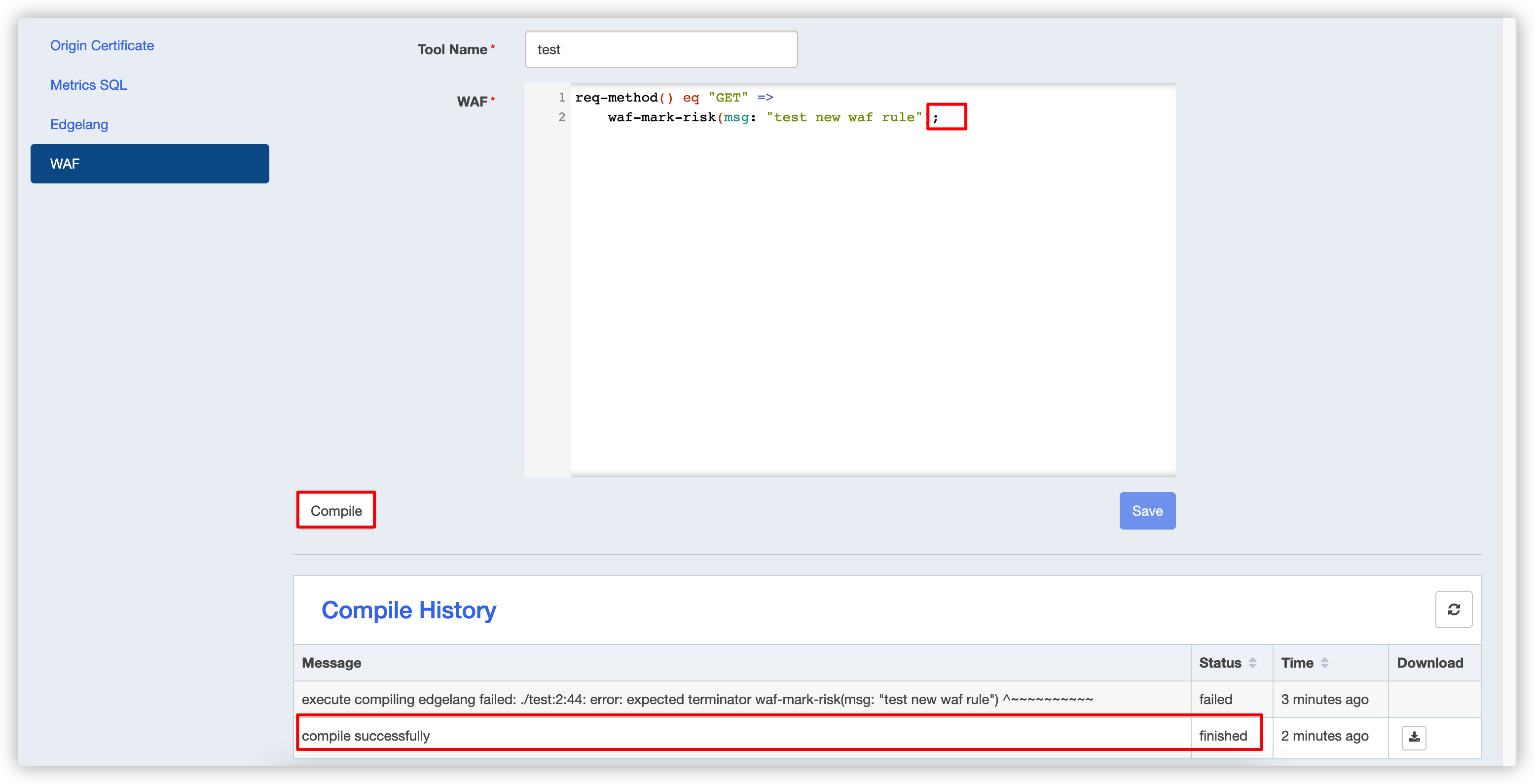
- Compile success
Modify the code with ; and recompile.
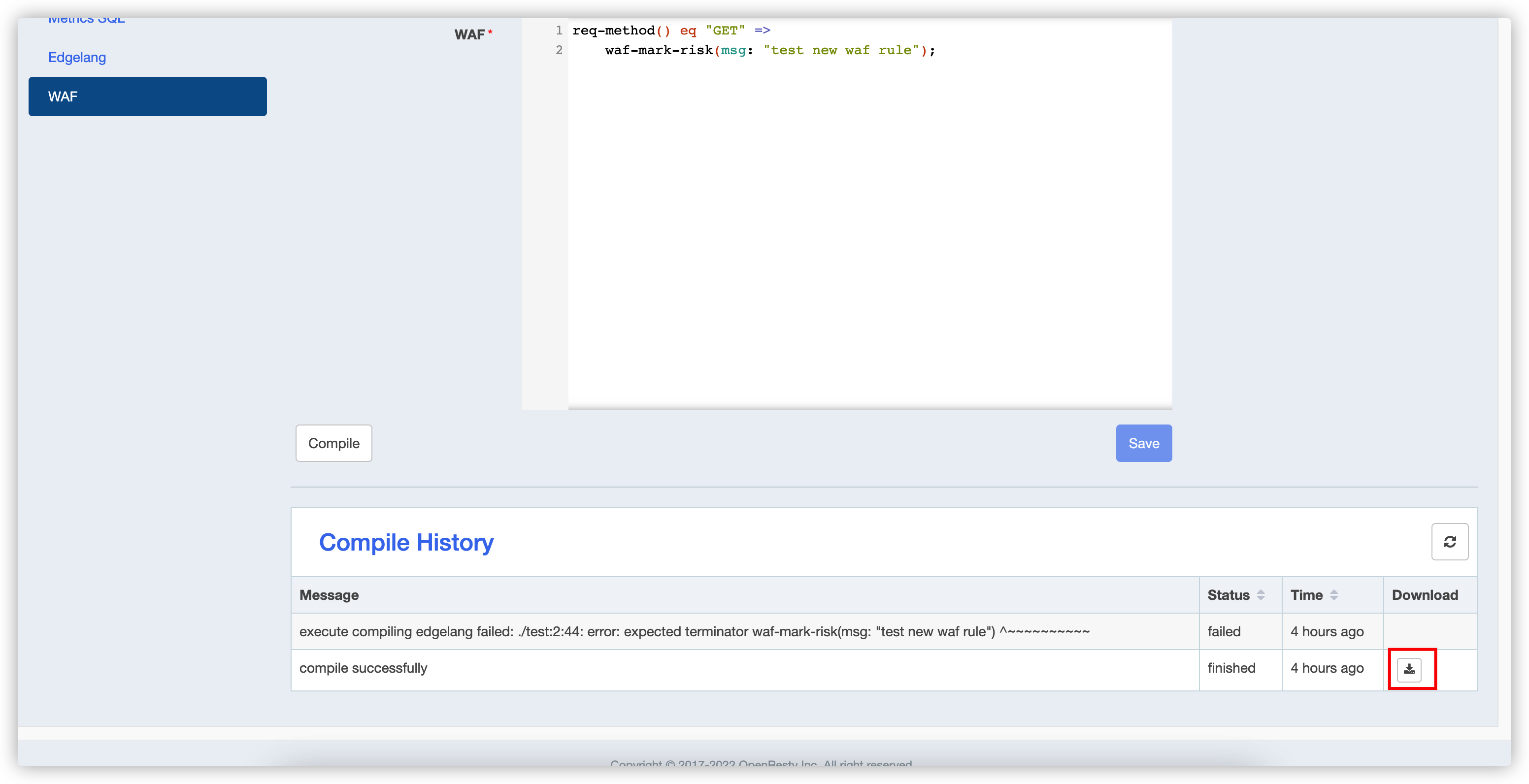
4. Download
- Download the compiled output file
3. Run
- Use the ruleset
location /t {
content_by_lua_block {
local orwaf = require "orwaf".new()
local res, err = orwaf:add_rule_set("my-waf-rule", "test")
if not res then
ngx.say("err: ", err)
return
end
local names = {
"my-waf-rule"
}
local matches, err = orwaf:run(names)
if not matches then
ngx.say("error: ", err)
else
ngx.say("ok: matches = ", require("cjson.safe").encode(matches))
end
}
}
add_rule_set(rule_set_name, rule_set_module_name)rule_set_name: Define a name for the ruleset, which will be used later to select the ruleset to be executed by name.rule_set_module_name: The name of the lua module produced by the previous compilation.
orwaf:run(rule_set_names)rule_set_names: The name of a custom ruleset, or the name of a built-in ruleset.
The names of all built-in rulesets are as follows:
- scanner_detection
- protocol_enforcement
- protocol_attack
- attack_lfi
- attack_rfi
- attack_rce
- attack_php
- attack_nodejs
- attack_xss
- attack_sqli
- attack_session_fixation
- attack_java